A virtual machine (VM) represents a software-based simulation of a physical server. For instance, consider your average desktop or laptop. Now, envision being able to additionally run an entire server system within it, separate from your primary system. Just like a physical server, this “server within a server” runs its own OS, applications, and stores data. This is made possible by virtualization technology, which partitions a single hardware unit into multiple, isolated devices.
What is a Virtual Machine?
The virtual machine, or simply VM, is fundamentally an abstraction from the hardware. Unlike the traditional approach of associating with the actual CPU, memory, storage, and network card, a VM works with virtualized counterparts of these components. A hypervisor, also known as VMM Virtual Machine Monitor, is a software layer that maintains and manages the physical hardware resources in the host system and is tasked with dividing these resources among the different VMs.

There are Two Types of Hypervisors:
- Type 1 (Bare-Metal) Hypervisors: These operate on the host hardware with no OS layer beneath them. Examples include VMware ESXi and Microsoft Hyper-V. These are used in cloud computing and data centers because they offer better performance and greater efficiency.
- Type 2 (Hosted) Hypervisors: These operate over an OS such as Windows, macOS, Linux, etc. Hosted hypervisors include VMware Workstation and VirtualBox, which are extensively used by individuals and in developmental settings.
In setting up a virtual machine (VM), you generate a file which encapsulates all the data necessary for the virtual pc to function. This data includes virtual hard disks, virtual memory, and even virtual network adapters. Then you install the OS of your choice (Windows, Linux, macOS) onto the virtual hard disk just as you would on a physical server.
Advantages of Virtual Machine
Virtual Machines have changed the paradigm of server use and activity, and today they are used by businesses or individuals. Improvements, especially when it comes to efficiency, cost and security, increase significantly with Virtual Machines.
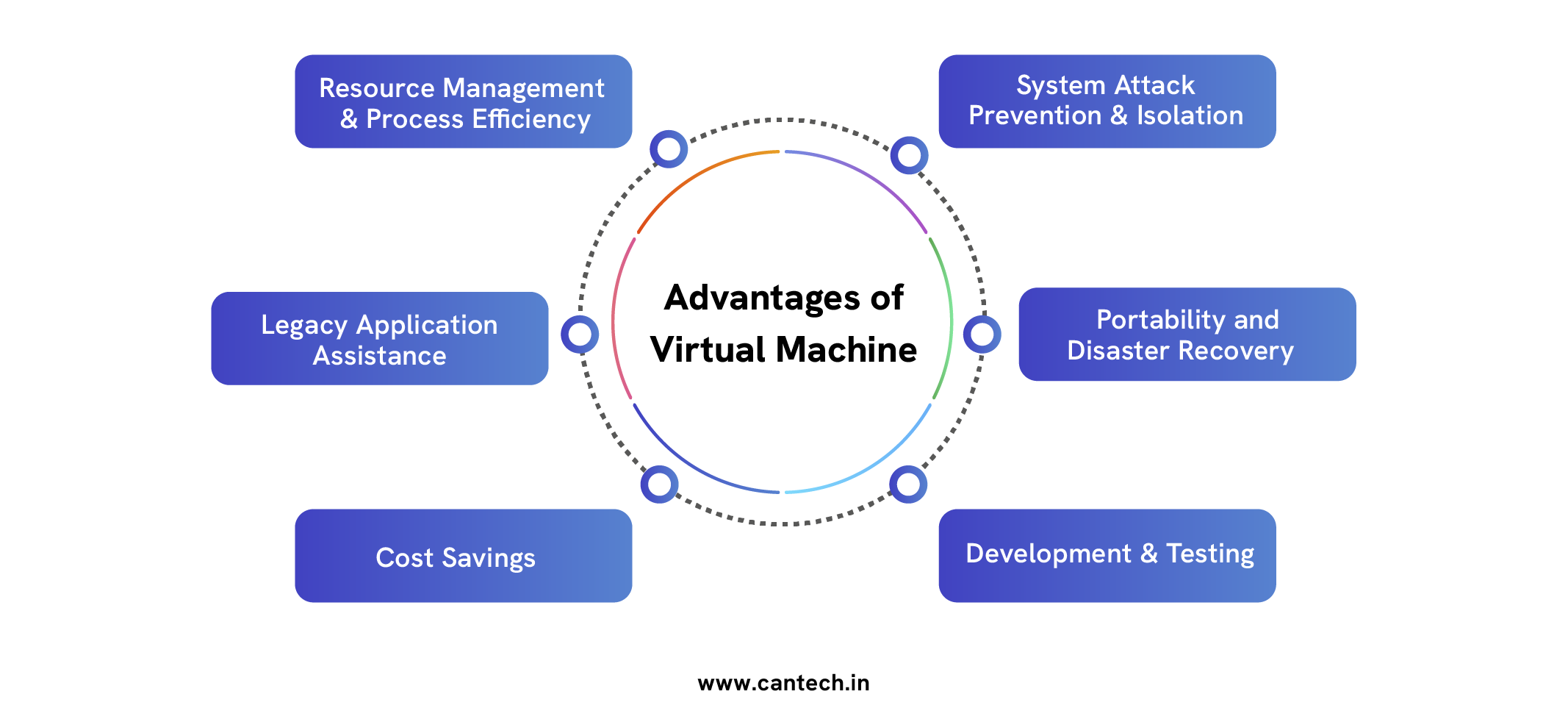
Resource Management and Process Efficiency
The use of VMs and virtual servers offers numerous advantages for companies, as they are capable of maximizing their hardware usage. Instead of using multiple physical servers, each running an application while sitting idle for most of the time, multiple VMs can be placed onto a single powerful physical server. This means:
- Reduced Initial Outlay: Companies can reduce their purchase costs and maintenance expenses by consolidating VMs onto a single physical server and reducing the number of servers purchased.
- Less Environmental Impact: A reduction in physical machines directly correlates to a reduction in electricity usage, which in turn decreases operational expenses alongside the company’s carbon footprint.
- Dynamic Resource Allocation: The hypervisor dynamically controls the CPU, memory, and storage resources within the VMs. If one VM requires more power, the hypervisor can reallocate resources from less active VMs, ensuring optimal performance overall.
System Attack Prevention And Isolation
Every virtual machine is an ecosystem on its own. This kind of virtualization brings about a number of different benefits such as:
- Security and Application Containment: If a VM encounters a crash or a virus infection, it will not carry over to other Vms in the same host or even the host server. This containment is of utmost importance for critical operations.
- Secure Testing Environments: Using virtual machines, IT specialists and developers may test new software, updates, or configurations without endangering the primary operating system. They have the option of restoring a clean virtual machine image in case something goes wrong.
- Sandboxing Suspicious Files: Email attachments and untrusted applications can be executed inside a virtual machine in order to ensure that if any damage is done, it would be well contained within a virtualized layer and would be easy to undo.
Portability and Disaster Recovery
The distinct characteristics of virtual machines make them especially resilient and portable:
- Easy Migration: Virtual machines can be stored as files, which allows for them to be easily relocated from one physical server to another, even if they are distant from each other geographically. This is a fundamental principle of cloud computing and supports concepts such as live migration, where the machine is moved without any downtime.
- Simplified Backups and Snapshots: Snapshots of virtual machines can be taken at certain points of time, allowing for fast reversion to a previously saved state should the need arise. This greatly aids in disaster recovery and system testing.
- Business Continuity: In case of a failure of a physical server, virtual machines can be powered on a different host system within a short time. This helps minimize service interruption and ensures business continuity, which is crucial for essential business functions.
Development and Testing
Virtual Machines are indispensable tools for developers and testers:
- Testing with VMs is indispensable in cloud computing. Users can run different testing environments of windows, and linux, or even older versions of applications with the same machine. Effectively saving time and resources.
- VMs reduce and eliminate the “it works on my machine” syndrome. Team members can make use of the same image and hence get the same results. Problems are easily solvable and environments are effective.
- Developers can make configuration changes, install and update libraries or code freely without any fears of breaking or damaging the main branch. Changes can be reverted without any time loss enhancing productivity.
Cost Savings
- Hardware expenses, streamlining power usage through equipment, reducing the number of physical servers to lower the electricity, have a direct impact on cooling cost and power consumption, lowering utility bills.
- Fewer physical servers result in lower maintenance, less replacement parts, and lower time spent devoted to hardware repairs walking hardware troubleshooting.
- Automation, deploying new virtual servers, and simpler control cuts down on administrative interactions that need to be dealt with. Fewer tasks and less time means less overhead.
Legacy Application Assistance
- Many businesses continue utilizing ancient applications which do not work with modern systems, software, or equipment. Virtual machines assist with:
- Using Older Operating Systems: You can build a virtual machine using older operating systems like Windows XP and install the legacy application to run seamlessly within that encapsulated space, thus preserving modern systems.
- Increases Value: Thus, the organization can keep using the application and avoid costly rewrites, thus increasing its value.
Disadvantages of Virtual Machine
It is important to put forward the drawbacks of virtual machine technology, even when the pros seem considerable. Identifying these limits helps in making the right decisions of where to use VMs.
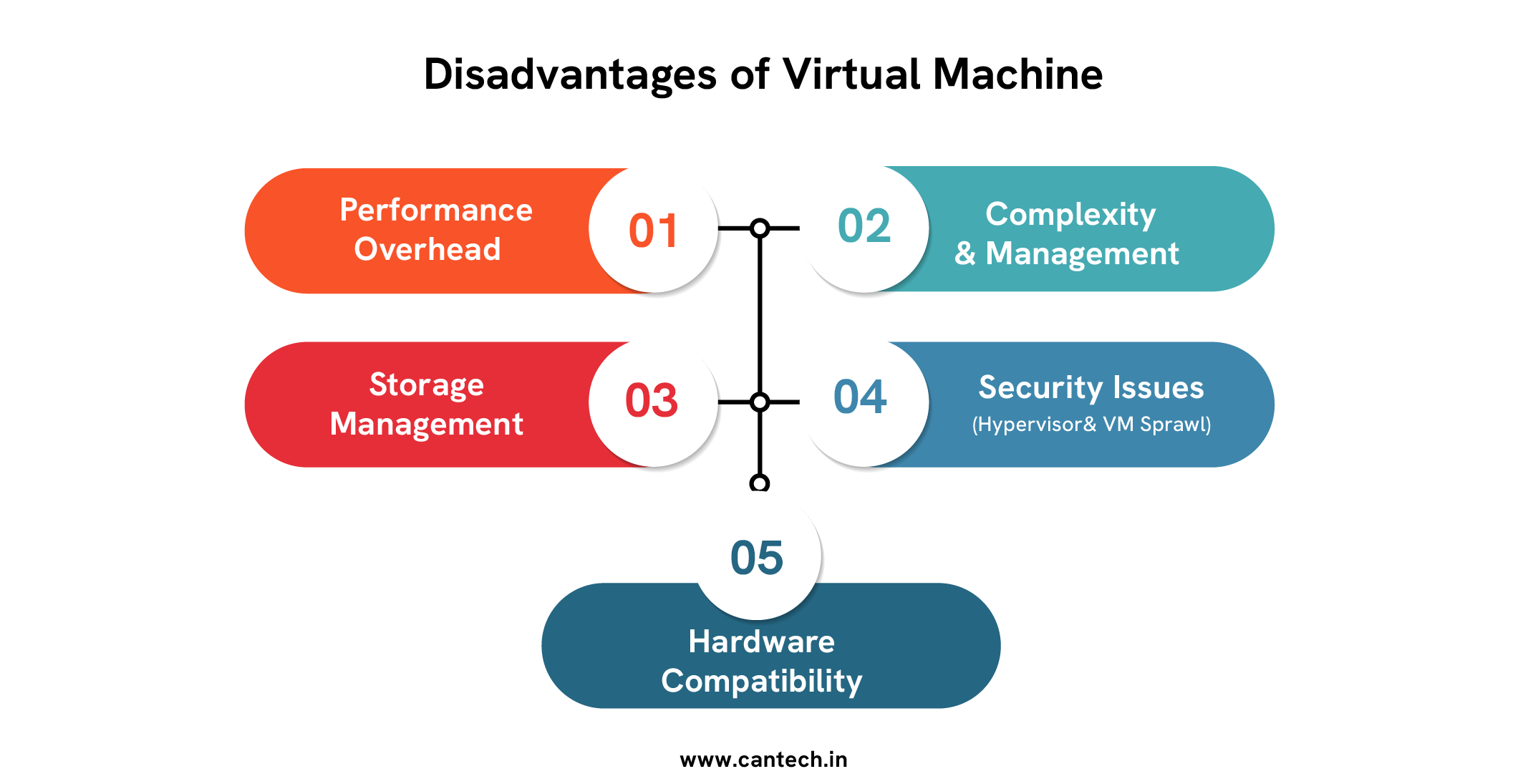
Performance Overhead
Adding abstraction between the guest OS and the physical hardware introduces what is virtualization. This layer, the hypervisor, incurs certain costs to maintain the VMs, and thus adds to the performance overhead:
- CPU and Memory Allocation: To function, the hypervisor requires computational resources. This means even if no virtual machines partake in active computations, a fraction of resources will inevitably need to be reserved for the virtualization layer.
- I/O Efficiency: Tasks, like reading and writing to a disk or monitoring network traffic, may become more sluggish in a virtualized system as compared to a physical system. This is because the requests for I/O must be handled by a hypervisor.
- Resource Contention: Performance for all virtual machines can be impacted if an overload of requests occurs simultaneously, such as during intensive file operations. This is referred to as “noisy neighbor” syndrome.
Video editing with dedicated GPU server, high performance gaming, or specific scientific simulations all require direct access to hardware components or are very sensitive to latency. These applications would not function optimally with a virtual machine setup.
Complexity and Management
Physical machines are often easier to maintain and manage compared to virtualized systems. While there are now advanced tools that allow for managing virtual machines, these offer a doubled edged sword as they come with added complexity.
- Initial Setup: Higher levels of technical skill are needed to install agreement devices, partition virtual machines, allocate resources, and install guest OSs than to cluster hypervisor setups.
- Resource Management: An effective resource allocation requires planning, as poorly planned structures can lead to unpredictable performance lags, and competing virtual machines may end up struggling due to resource bottlenecks. Efficiency inferred with straddling too many or too few resources may become an issue.
- Troubleshooting: Diagnosing problems within a virtualized environment is multifaceted as both the guest operating system and hypervisor/host layer need attention.
- Licensing: In a virtualized environment, licensing software considering the operating system and applications becomes more challenging. Vendors may have differing licensing policies for physical versus virtual deployments which undermines expected cost benefits.
Storage Management
An essential part of any IT infrastructure is storage. Storage poses unique challenges in virtualized environments:
- Storage I/O Demands: As virtual machines are consolidated onto a single host, the cumulative storage I/O needs may be significant. Also, without sufficient performance from the underlying storage systems, the storage systems may become the bottleneck with respect to virtual machine performance.
- Shared Storage Complexity: In corporate environments, virtual machines rely on shared storage systems, like SANs and NAS, which increases the complexity of configuration to manage virtual machines.
- Snapshot Overhead: Although snapshots enable users to preserve the current state of a virtual machine, unmanaged excessive snapshots can degrade performance due to the creation of additional data blocks required to track changes over time.
Security Issues (Hypervisor and VM Sprawl)
While virtual machines (VMs) provide a degree of isolation, there are still some concerns that require special attention to security:
- Hypervisor Issues: As a key component of a virtual system, the hypervisor must be adequately safeguarded, as an attack on it or its counterpart VMs would escalate into an even bigger problem.
- VM Sprawl: Ease of creating VMs all too often leads to rampant, uncontrolled proliferation of VMs within an organization. Aside from resource and security risks, redundant VMs are also capped redundant VMs are redundant sprawl.
- Patching Processes: Each virtual machine has its own designated operating system and software applications, thus from an administrative perspective, the burden triples when patching processes need to be conducted.
Hardware Compatibility
Most new machines come with support for virtualization built-in, but parts from older machines, as well as some high-end specialized equipment, might not fully align with this approach. This could pose an issue for some scenarios that prioritize direct hardware access.
Virtual Machines in Cloud Computing: Partners in Progress
Cloud computing relies on virtual machines as one of its foundational components. In fact, VMs make most cloud offerings possible, especially IaaS (Infrastructure as a Service). When you order a virtual server from cloud providers like AWS, Azure, or Google Cloud, you are in essence renting a cloud-hosted virtual machine.
Read More : What is Cloud Computing
The Operating Model of Cloud Providers
There are huge physical servers in a cloud provider’s data centers. These servers require enormous amounts of computing power. Using these servers, cloud providers take advantage of virtualization techniques and divide the physical servers into a large number of VMs for their customers. This enables them to:
- Achieve Multitenancy: Customers share the same physical hardware, but their applications and data remain protected behind the curtains within their respective VMs, which gives users the cost benefits of cloud computing.
- Scalability and Flexibility: Cloud consumers can swiftly spin up new VMs to handle traffic and turn them off during non-peak periods. Expenditure is limited to what is actually used, illustrating the scalability offered through cloud computing.
- Resource Pooling: Computing and networking resources, as well as storage, can be pooled in large quantities and allocated dynamically to virtual machines as needed.
- Global Reach: Users can access VMs from different geographical regions and availability zones, which ensures redundancy and provides low-latency access to global users all over the world.
What is a VM in the Cloud?
A virtual machine (VM) in a cloud-based infrastructure is closely comparable to the one you use on your PC, with one key difference: it offers more benefits due to:
- Managed Infrastructure: Everything from the physical equipment DATACENTER, CONTAINER, up to the logistics storage, hypervisor, and above is handled by the cloud service provider. Users no longer need to worry about safeguarding their data centers, enabling ease of use.
- APIs and Automation: At the cloud ecosystem level, APIs and CLI are made available to users. VMs automation scaling, management, and creation is made easier on the user’s end with cloud services, thus supporting DevOps methodologies.
- A Range of Offerings: Cloud service providers have diversified virtual machines. For each other “instance type” there are several units of CPU, RAM, and Storage offered. Thus users are exposed to a variety of options to suit their workloads.
Virtualization enhances efficient resource sharing, scaling on-demand, and creates highly available and resilient services.
Critical Characteristics Of Virtual Machine Software
All users of hypervisors and Virtual Box, VMware, and Workstation have special features tailored to improve management of the virtual machine software.
Snapshot Control
Capturing the exact condition of a VM is possible with this feature. If a risky change is about to be made, a snapshot can be taken, so in case something goes wrong, the changes after that point can be undone. This approach is useful during development, testing, and in disaster mitigation.
Cloning
Creating an exact duplicate of the existing VM can be achieved through cloning. This is useful for:
- Quick Deployment: Allows the instant setup of multiple identical VMs required for testing or production purposes.
- Base Environment: User profiles are created for specific users and projects by cloning a master image, enabling support for those specific users or projects.
Network Configuration
Using virtual machine software, network configurations may be set as follows:
- Bridged Networking: The VM operates as a standalone node on the network and receives an individual IP address.
- NAT (Network Address Translation): Basic internet access for a VM can be achieved simpler than this. A VM could access the internet through the host’s IP address.
- Host-Only Networking: A VM has some limited ability to interact with other servers, but can only fully communicate with the host system and is thus insulated from the internet.
- Internal Networking: Through internal networking, Virtual Machines situated within the same physical machine can exchange information with other VMs, but cannot access external networks. This is beneficial when testing multi-tier applications.
Resource Allocation
Similar to other types of resources, the CPU, memory, and disk space are allocated for each virtual machine (VM) individually. This separation prevents resource contention between virtual machines, protecting their essential functions, such as critical application processes.
Shared Folders and Drag-and-Drop
To enhance functionality between host and guest operating systems, VM Software has developed the following features:
- Shared Folders: This feature enables specific folders on the host system to be accessed from within the VM.
- Drag-and-Drop: This allows for file transfers between the host and guest systems with no need for cumbersome steps.
USB Device Passthrough
Virtual Machines (VMs) can connect to and interact with external USB devices such as hard disks, printers, as well as specialized equipment like hardware security dongles as if they were directly attached.
Remote Access
Most VM solutions, especially enterprise and cloud offerings, include remote access capabilities. Control and management of virtual machines located in other areas of the globe is possible as long as there is Internet access.
A Simplified Look At How Virtual Machines Work
To explain the working details of virtual machines, it is important to first outline hypervisor and virtualized hardware, as well as the concept of virtualization.
A hypervisor manages multiple virtual machines (VMs) from a supervisory level. Each VM possesses its own hypervisor. At the time of powering on the VM, the hypervisor intercepts the lower level request calls to the hardware and does not simply allow access to the actual hardware. The hypervisor doesn’t just forward commands of the VM to the physical server, but transform them into formats understandable by the VM in order to provide simulated hardware resources.
Let us consider the following:
- Virtual CPU: For the commands targeting the VM’s CPU, the hypervisor will issue commands to the real physical CPU cores. For each VM, the hypervisor has the option to either limit the use of a core to a fraction of its time or provide full access to an entire core.
- Virtual Memory: The hypervisor manages the mapping between the VM’s memory addresses which are virtual and the host’s physical memory addresses. Thus, some portions of the host RAM have to be allocated as memory resources for the VM.
- Virtual Disk: The hard disk of a virtual machine is often regarded as an over-proportioned file located on the physical disk of the host machine. The hypervisor processes reading from and writing to the virtual disk as file operations. Therefore, in cases where the virtual machine attempts to read from or write to its disk, the hypervisor implements appropriate strategies to fulfill these requests.
- Virtual Network Adapter: Within the VM, a virtual network interface card (NIC) exists. The hypervisor constructs a virtual switch that links this NIC with the host’s physical network card, allowing the VM to access the global network for communication.
The efficiency with which all virtualization features are executed is one of the leading factors as to why virtualization is powerful and practical. Due to the hypervisor’s constant managing and translating work on the VMs, distinct full-service VMs are able to run parallel and self-contained within a single server alongside the host’s OS.
What is a VirtualBox?
VirtualBox is an open-source virtualization program offered free of charge by Oracle Corporation. It can be classified as a Type 2, or “hosted,” hypervisor. Unlike bare-metal hypervisors which directly utilize physical hardware, VirtualBox functions as an application on the Windows Host OS Desktop. This approach is very beneficial for individuals, developers, and small companies because there is no need for specialized server hardware.
In VirtualBox’s VMs one can accomplish creating, and configuring multiple virtual machines (VMs) each able to optimally emulate physical computing resources such as a CPU, memory, storage, and network cards as peripherals. It is possible to install several guest OSs, ranging from Windows and many distributions of Linux, macOS (Apple specific hardware) to even older and rare operating systems. VirtualBox’s versatility enables users to test new software, experiment with system configurations, run legacy applications that do not suit the main operating software used, and run more securely browse the web.
Conclusion: Effects of Virtualization Are Still Relevant
Virtual machine advantages and disadvantages cannot be underestimated as they have dramatically transformed the IT landscape. Individual developers can work in isolated environments using VMware Workstation and VirtualBox. Businesses and enterprises have built scalable infrastructures on cloud-based VM architectures, enabling self-service from public clouds and benefiting from unparalleled flexibility.
There is no doubt that virtual machines have become a necessity for modern IT. Although they have evolved over time, their unmatched advantages of improving resource use, automation, reduced costs, portable access, strong security through segregation, and powerful fault-tolerance mechanisms cannot be overlooked.
FAQs
What is Virtual Machine?
A virtual machine is an emulation of a computer done by software that has the capacity to operate its unique operating system and applications. It allocates resources to a single physical machine called a host, and allows numerous isolated guest operating systems to function at the same time.
Are Virtual Machines 100% Safe?
Unfortunately, the answer is no. Because of certain potential weaknesses of the hypervisor, software that runs virtual machines, others may use malicious techniques for security breach. Nonetheless, the hypervisor is considered to possess an adequate degree of isolation virtualization table for at least to test malware and safe browsing.
What are the Advantages and Disadvantages of Using a Virtual Machine?
Some of the advantages comprise better usage of resources, as in executing several operating systems in one server, and layered security isolation improved from one in a host machine to several in guest machines. This is because an infected guest operating system is prevented from causing damage to the host.
Some of the disadvantages may relate to the sharing of resources resulting in execution overhead, and the increased complexity of managing resources compared to managing a single host machine.
What is the Benefit of Virtualization if a Host Machine is Damaged?
One of the advantages is that, with virtualization, disaster recovery and business continuity is guaranteed, as the virtual machines are software oriented, so they can be easily moved or restored from a backup to any new healthy host machine, keeping downtime to a minimum. This is called easy portability.
Which Factor does not Impact the Cost of Running a Virtual Machine?
In some cases, networking hardware and software costs (in an on-premises configuration, and if considered a fixed or isolated cost) is considered not to be a point of concern when discussing the cost of a VM instance as opposed to CPU, memory, storage, and OS licensing, which are all costs that depend on variable resources.