How to Bypass the HTTPS Warning for Self-Signed SSL/TLS Certificates?
Introduction
Many web applications deploy with self-signed TLS/SSL certificates to encrypt traffic during the initial configuration. When connecting to such applications, browsers often display security warnings because the certificate is not issued by a trusted authority. While these warnings help protect users from potential security threats, they can be bypassed when accessing a known and trusted site with a self-signed certificate.
This guide explains how to bypass these warnings in different web browsers and proceed to the site. Keep in mind that while self-signed certificates provide encryption, they do not offer the same level of trust and verification as those issued by a certificate authority.
Firefox
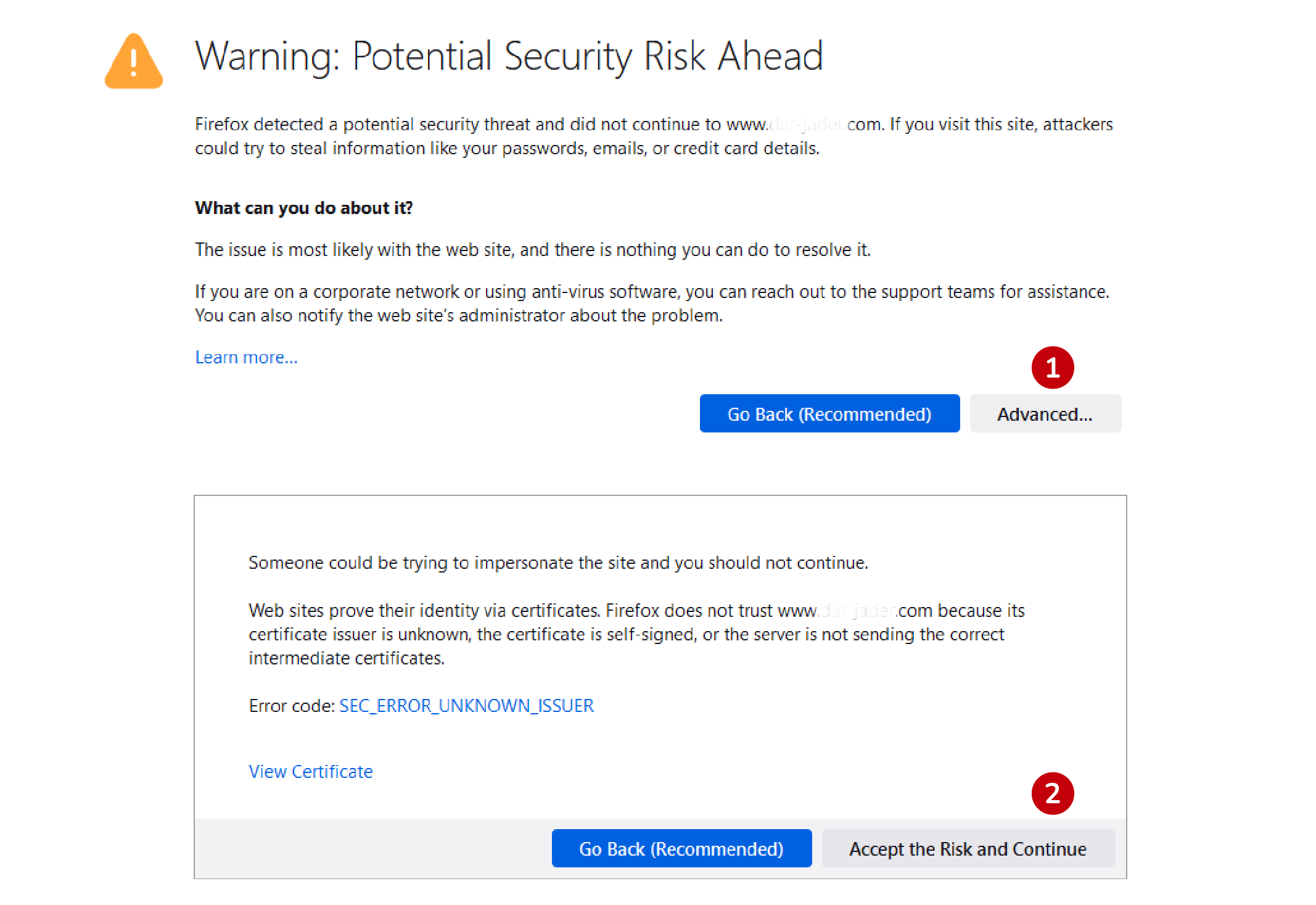
Firefox offers a straightforward way to bypass the warning.
- Click the Advanced button.
- Select Accept the Risk and Continue to proceed to the site.
Safari
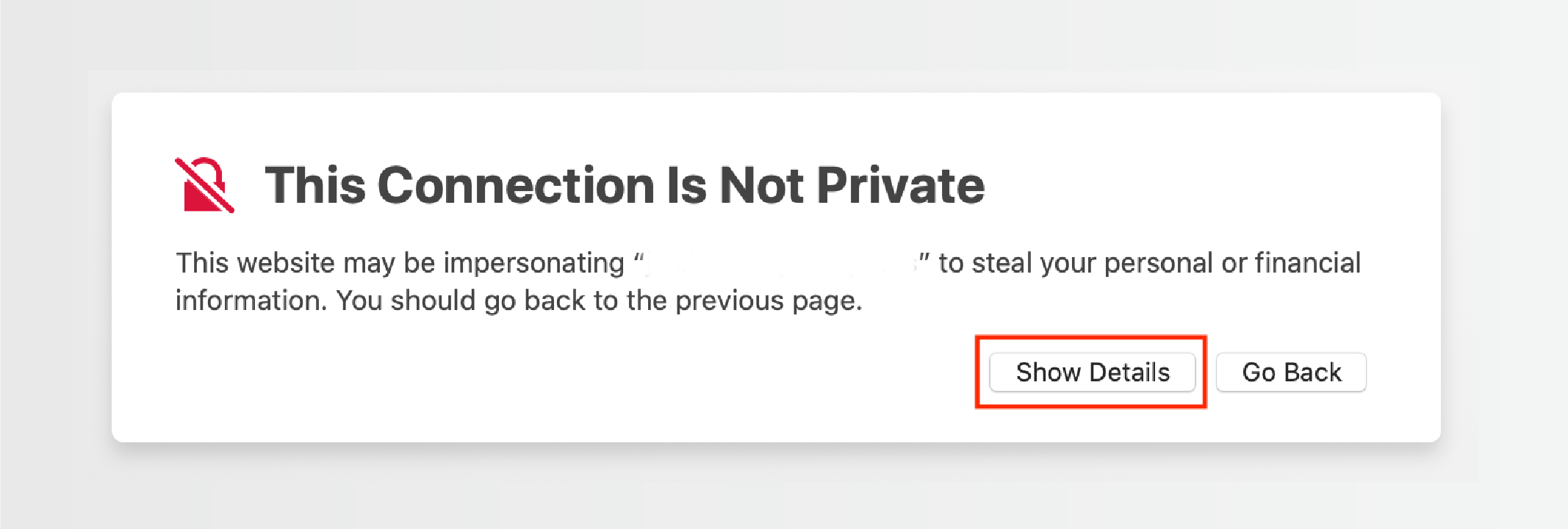
Safari displays a security warning when encountering an untrusted certificate. To bypass it:
- Click Show Details to expand the warning message.
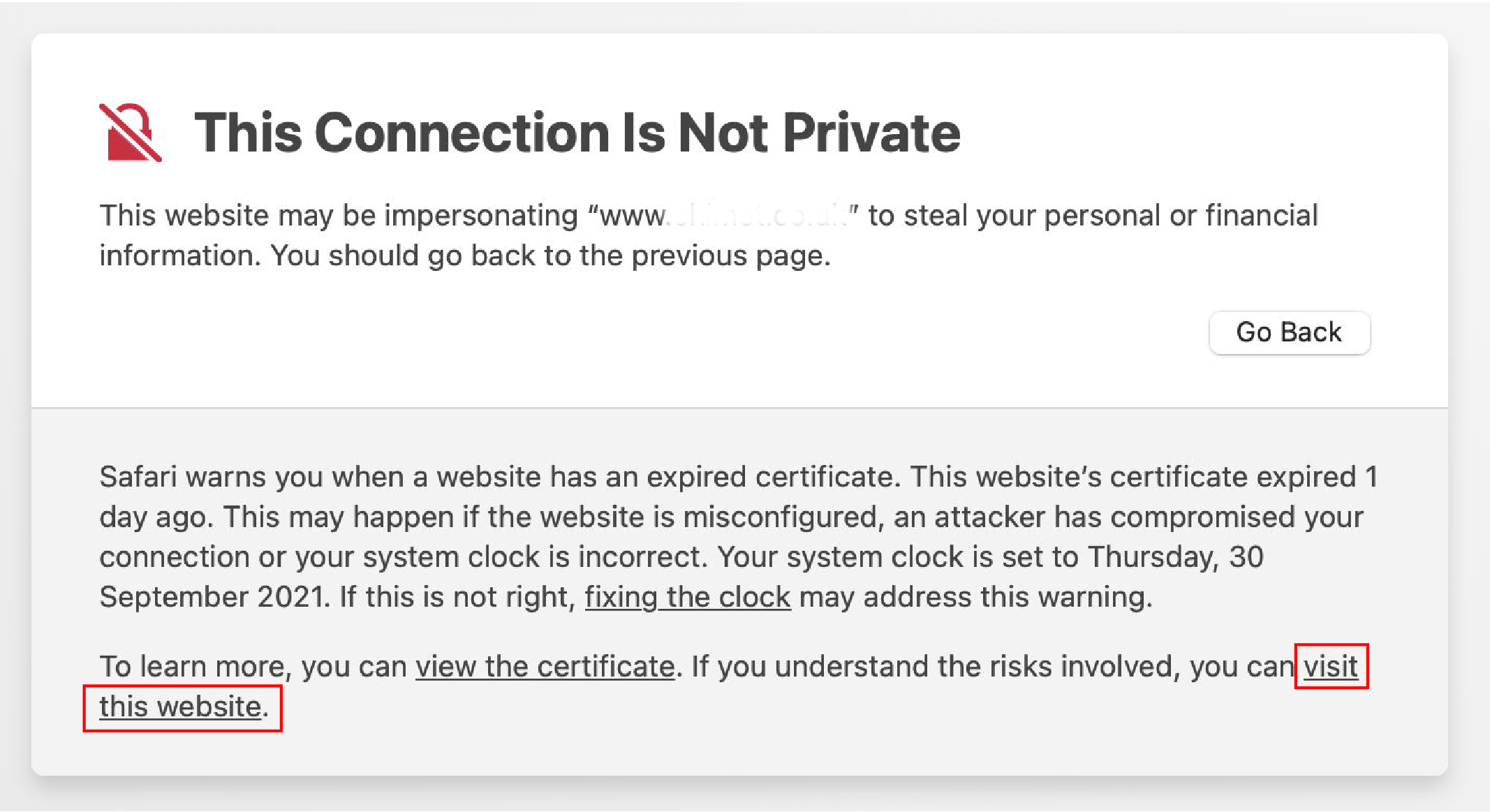
- Click the link to visit this website.
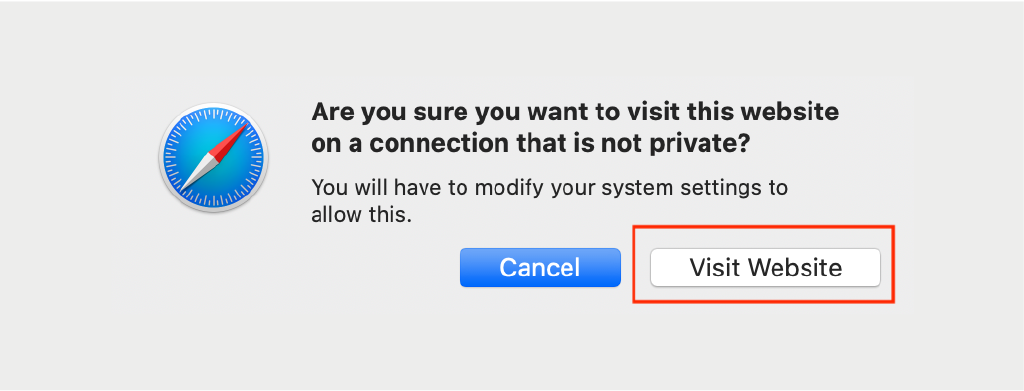
- A confirmation dialog will appear; click Visit Website to continue.
- If prompted, authenticate using Touch ID or enter your password to modify the certificate trust settings.
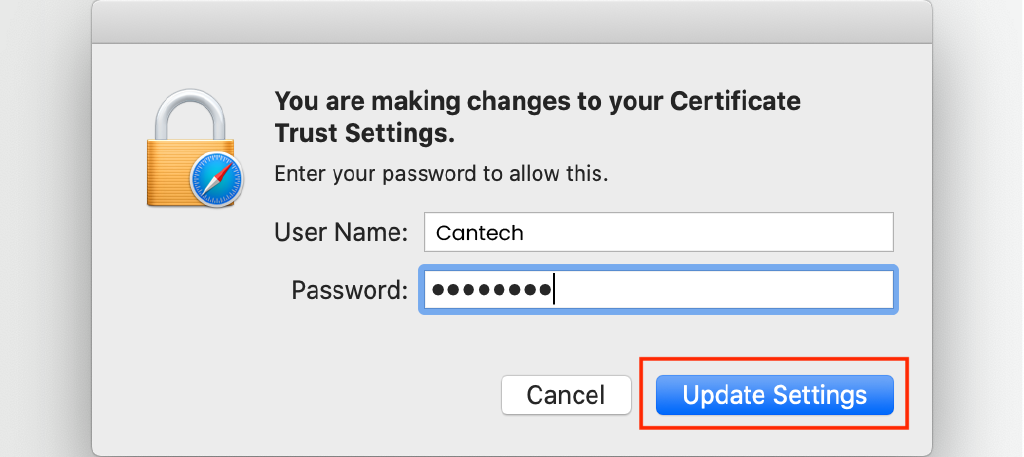
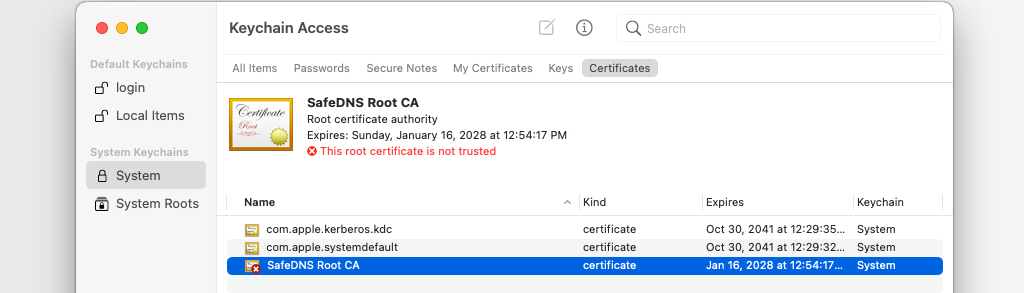
If you want to remove the certificate later, open Keychain Access, locate the certificate in the login keychain, and delete it.
Chrome
Recent versions of Chrome have made it more challenging to bypass security warnings. On some systems, you may still find a Continue to… link after clicking Advanced, but on macOS, this option is often hidden.
To bypass the warning manually:
- Click on the page to ensure it has focus.
- Type the phrase: thisisunsafe (without an input field, just typing will work).
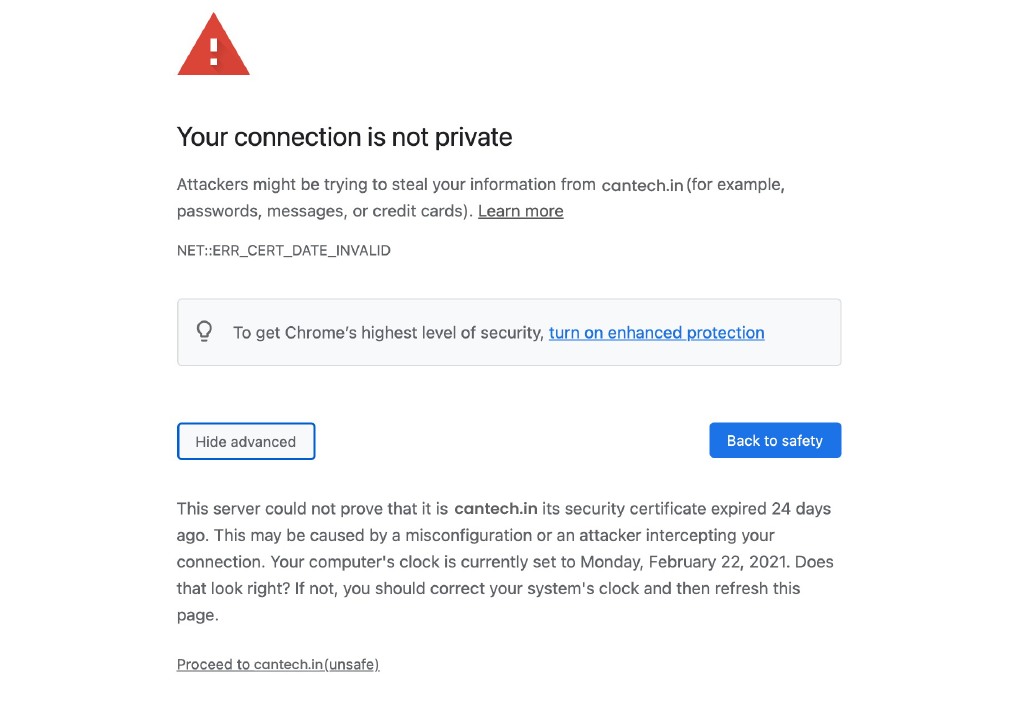
- If this method stops working in future Chrome updates, the developers may have changed the phrase.
Re-enabling Warnings
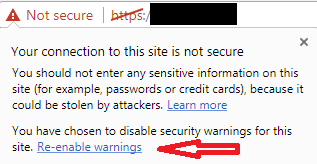
If you have used this method and want to restore security warnings, click the Not Secure flag in the address bar and select Re-enable warnings from the panel.
Brave
Brave, being based on Chromium, follows the same security warning process as Chrome. You can bypass warning by using the phrase: thisisunsafe
Edge
Microsoft Edge, also built on Chromium, has a slightly different warning page but allows bypassing in two ways:
- Click the Advanced button.
- Select the Proceed to… link to proceed.
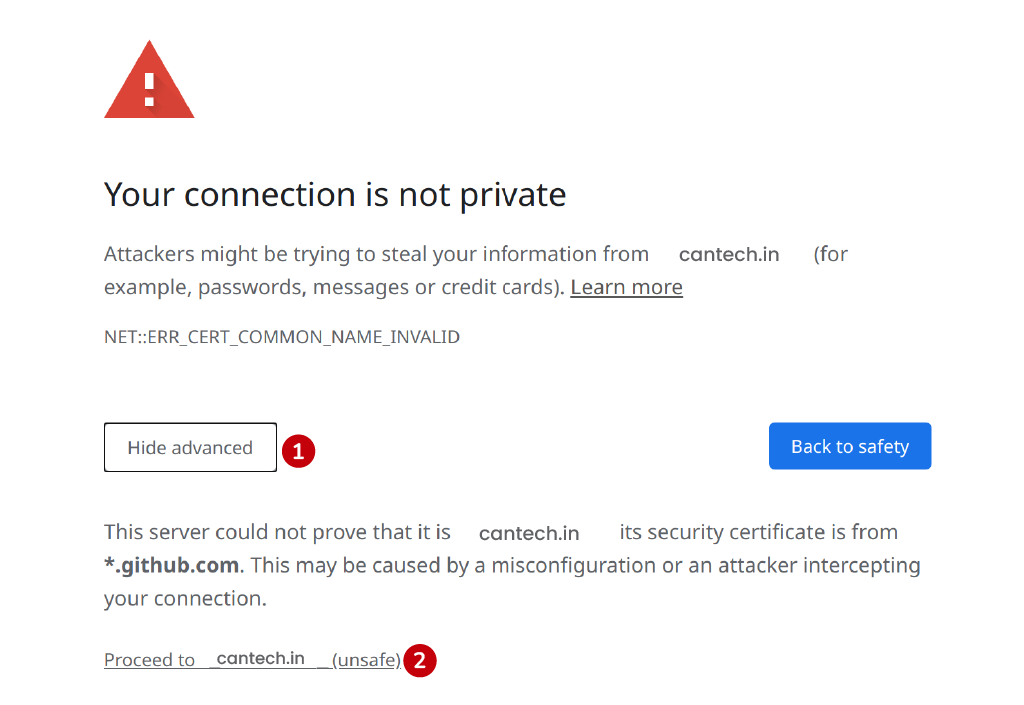
- As an alternative, type the phrase: thisisunsafe
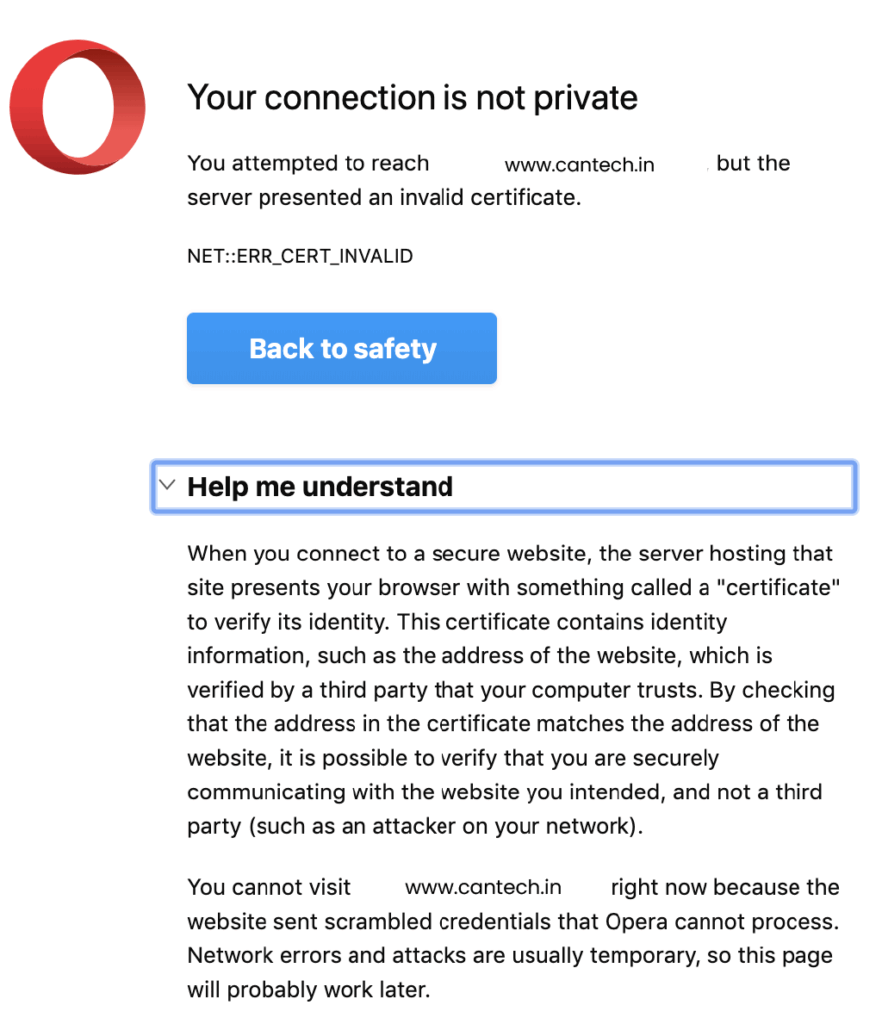
Opera
Opera, another Chromium-based browser, follows the same method as Chrome. Typing ‘thisisunsafe‘ on the warning page will allow access.
Understanding Self-Signed Certificates
TLS/SSL certificates enable encrypted HTTPS connections, ensuring secure data transmission. Trusted certificates are issued by recognized certificate authorities, while self-signed certificates are generated by the server itself. They provide encryption but lack third-party validation, which is why browsers flag them as untrusted.
For websites with a registered domain name, obtaining a free certificate from Let’s Encrypt or another certificate authority is recommended. However, in cases where a domain is not yet set up, or encryption is required for local development and testing, self-signed certificates offer a temporary solution.
While modern browsers enforce strict HTTPS policies, they still allow users to override warnings for trusted connections when necessary. However, it’s important to ensure that self-signed certificates are only used in secure, controlled environments.
Conclusion
Self-signed TLS/SSL certificates can serve as a means for traffic encryption and securing connections, specifically during the initial installation or while developing locally. Because they are not validated by a trusted certificate authority, popular websites viewed in today’s web browsers will indicate that they are untrusted and the user must bypass security warnings. This can be an inconvenience, but it is necessary to avoid potential attacks or security risks.
Most browsers will handle trusting untrusted certificates in various ways. Some Browsers will allow users to bypass warnings and others are less straightforward and require more hidden commands to override. This allows users access to trusted sites with self-signed certificates and should be done with caution, like bypassing warning messages. Always beware when overriding security warnings to avoid access to known bad websites. However, generally, self-signed certificates should be replaced with trusted certificates whenever possible, especially for production use.
Over time securing a website with an existing TLS/SSL verified certificate is the best case. This allows users access to the websites with no warning messages in their browsers, help people build trust, increase credibility for web sites, and finally increase overall security. However, if using self-signed certificates, they should be used in a controlled environment with appropriate procedures to ensure protection and compliance of available data.