In the case of a website or application infrastructure, a reverse proxy operates as a protective shield that could enhance security, speed, and scalability. Increasing amounts of web traffic along with the evolution of cyber threats helped reverse proxy servers gain prominence as an important aspect of data delivery and protection over the internet.
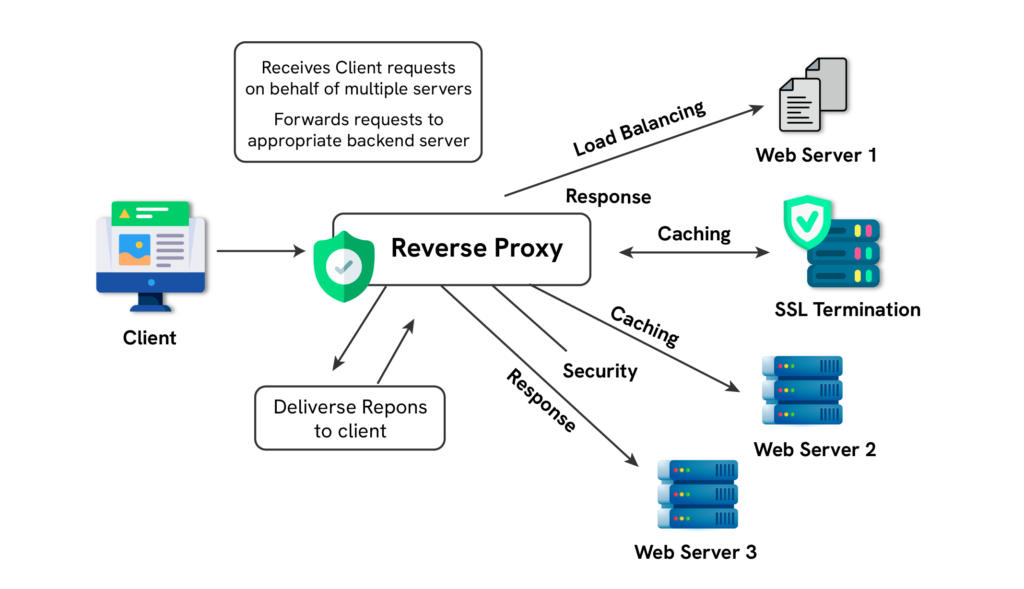
A reverse proxy acts as a barrier and handles client requests while requesting data from an origin server on the client’s behalf. He or she will send the client’s requests to one or more backend servers according to some set of policies, and the reverse proxy server fetches the required information. An organization would be able to manage traffic, resource allocation, and sensitive information with this configuration.
With queries like, “What is a reverse proxy?”, “Reverse proxy definition,” or, “Do I need a reverse proxy,” It seems like you’re searching for explanation and context at the same time. In this case, I can say you are at the right place. In this article you will learn what a reverse proxy is, how it works, and its importance for modern web infrastructures that demand speed, security, and high-performance. These pointers are valuable regardless if you are running an online eCommerce store, a SaaS platform, or enterprise-grade applications; they can enhance your infrastructure strategy.
What Is a Reverse Proxy?
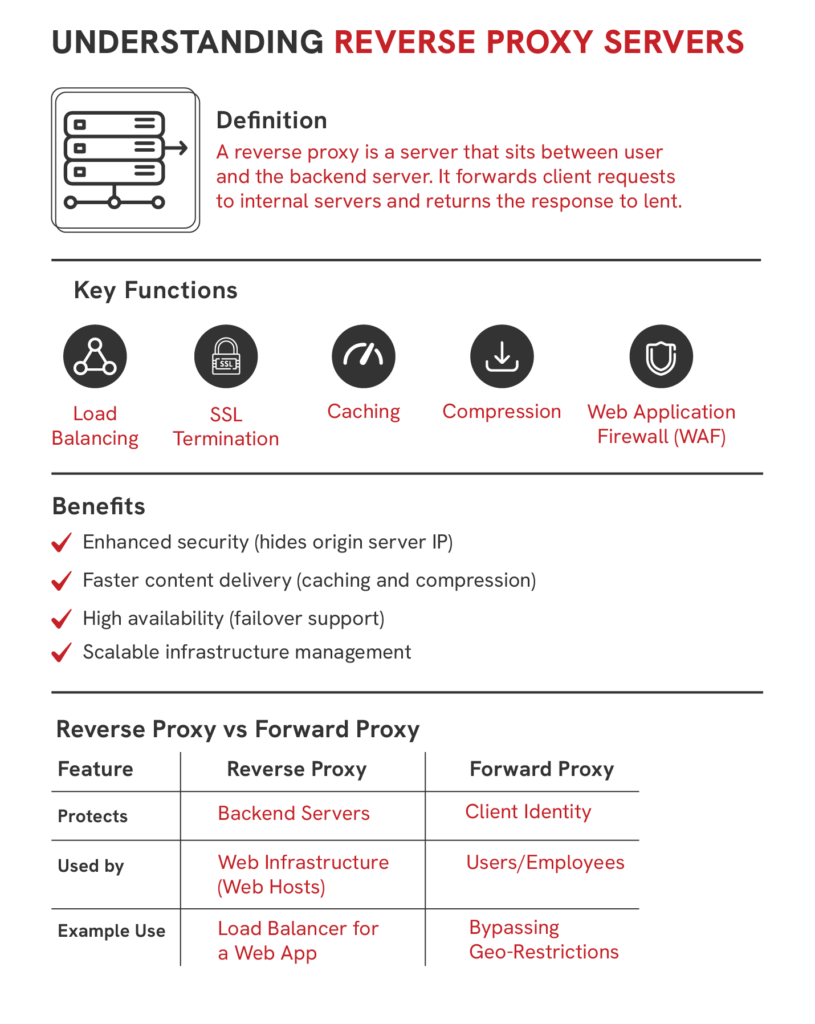
A reverse proxy is a proxy server that is positioned in front of one or more back servers and aims to handle the client calls to the backend server. Unlike a forward proxy which aims to safeguard the clients by protecting their identities, a reverse proxy aims to safeguard the back servers by managing the back server’s identities and controlling the traffic. It is a proxy that protects your internal network and serves as a gatekeeper.
Companies often utilize reverse proxies to optimize site performance, improve security, and increase reliability. Reverse proxies perform various functions such as load balancing between different servers, caching static content, compressing files, and managing SSL encryption to free backend resources. These functions increase content delivery speed, and reduce load on backend resources.
Apart from improving performance, reverse proxies also improve security by preventing access to backend systems and infrastructure, acting as a security buffer. This makes the infrastructure significantly less susceptible to DDoS attacks, brute-force attacks, and data leaks. Businesses of all shapes and sizes utilize reverse proxies as part of a Secure Scalable Architecture, especially during High traffic volumes or when sensitive user data is involved.
How Reverse Proxy Works?
Forward Proxy vs Reverse Proxy: Key Differences
The two types of proxies, reverse and forward differ in where they sit in a network, even though they are both proxies.
Forward proxy servers are used by clients to access content behind a specific block. Through concealment, it enables users to bypass geo-restrictions, access blocked websites, or surf the web anonymously.
1. The Purpose and Direction
A forward proxy assists a client by making outbound requests on their behalf. A forward proxies primary purpose is to detect and prevent misuse of the client’s identity and access control systems. A forward proxy is a mediator between the client and different web servers and hides the IP address of the client from the web servers. This is common in business environments. A person trying to access restricted content or trying to enhance their digital privacy may use this arrangement. A web server does not know the real client’s IP address and only sees the address of the forward proxy.
In contrast, a reverse proxy filters inbound requests from the internet to one or more web servers. A reverse proxy serves the purpose of concealing the servers, balancing the load of incoming requests, as well as enhancing the server’s performance. A reverse proxy fetches requests from multiple clients as an intermediary proxy and forwards them to the appropriate backend server. From the client’s perspective, only the reverse proxy’s IP address is visible. As a result, the backend servers are sheltered from disclosure. This is crucial for certain applications and websites that deal with numerous requests, especially when security and speed are a top priority.
2. Security and Anonymity
A forward proxy provides anonymity to the clients, hence, anonymizing them. A forward proxy enables clients to navigate the web without exposing their IP addresses. A forward proxy can also serve as a security measure by blocking harmful or inappropriate websites and content, thus helping clients to avoid accessing dangerous material. Regardless of the risks, the forward proxy does not protect the web server from which it gathers information, as the forward proxy focuses solely on the client side.
A reverse proxy provides anonymity and security for the server. It protects the backend servers from being directly accessed via the internet, which can reduce the risk of direct attacks. It can also function as a Web Application Firewall (WAF) and scan the web for incoming traffic consisting of harmful requests to defend against common web attacks such as SQL injection or cross-site scripting. In this case, the reverse proxy serves as the primary and sometimes the only perimeter security against external attacks.
3. Functionality and Use Case Scenarios
A forward proxy actively performs functions such as filtering content, caching data for quicker retrieval, and circumventing firewalls. One relevant example would be an organization that monitors and controls employee internet access through the use of forward proxy. Another example could be an individual using proxy servers to access content that is blocked in their region. The forward proxy aids in client-side network management settings, making it a lot easier to manage the network and policy enforcement for a number of users.
Key functions of a reverse proxy include balance server loads, SSL termination, and storage of content caches. A reverse proxy allocates incoming requests to a number of back end servers so that no single server is overloaded. A reverse proxy is capable of performing SSL encryption, thus relieving the web servers from performing this demanding process. Examples would be serving high traffic, large scale sites, e-commerce businesses, and cloud services that require enhanced performance, security, uptime, and scaling. A reverse proxy acts as a server tool and improves the speed of content delivery to numerous users.
In contrast, reverse proxies are employed by web servers to manage and secure incoming client requests. A reverse proxy conceals the backend infrastructure, balances traffic, caches content, and protects against cyber threats.
The Client’s Proxy: Understanding the Web Proxy
A web proxy, or forward proxy, serves as a foundational component in network infrastructure. In simple terms, a proxy server is a middleman, processing requests made by a client. The client requests data, and the forward proxy server retrieves it on the client’s behalf by requesting it from the internet. The proxy server is a client’s gateway to the internet and not the other way around, further explaining the utility of proxy servers. This is different from a reverse proxy and is primarily targeted for individual users or corporate intranets for limiting access and controlling outbound traffic.
To increase security, privacy, and performance, a forward proxy operates with a specific user in mind. It provides a certain level of privacy by concealing the user’s IP address, and consequently, websites find it difficult to track users. In addition, it’s common for proxy servers to store content that is requested frequently. Network bandwidth is preserved, and Browsing becomes more efficient when server response times are reduced. Although a forward proxy does not provide the same level of protection a VPN would, it can still filter content and guard a user’s privacy, providing notable, actionable advantages.
To forward and reverse proxy, There are intrinsic differences which make them useful in different situations. In the rest of the blog, a reverse proxy will be elaborated on, which serves the web server, while a forward proxy serves the client. A proxy can be used for personal reasons, and while anonymity, security, and privacy come into play, the proxy provider should be reputable. Anonymity provided by the proxy might not be worth it; if set up poorly, users could face web-based hacks, privacy breaches, or more. Thus, an informed decision will go a long way in harnessing the benefits of a forward proxy.
Advantages of a Reverse Proxy
The growing responsibilities of a reverse proxy server are becoming clear with the increasing scale of modern websites and applications. A reverse proxy server performs the functions of a secure proxy server, providing intermediaries between clients and backend servers, and offers other equally important operational and security advantages that are essential in a high traffic environment.
What is a Reverse Proxy Server? A Deeper Dive into Its Functions
A reverse proxy server accepts and fulfills client requests that are meant for backend servers. The reverse proxy server does what is required on its end and forwards the response to the client. Because proxies are able to do more complex things that include traffic routing, caching, SSL processing, request Filtering, and protection of the backend servers, they can also provide advanced services. As opposed to the traditional setups where the client requests are directly going to the origin server, reverse proxy systems are able to save a great deal of traffic and also drastically improve user experience and backbone resilient infrastructure.
Performance Optimization
Load Balancing Services
One of the most important functions of a reverse proxy is performing load balancing services. In high traffic scenarios, a reverse proxy allocates incoming requests to several backend servers to make sure that no one server is processing too much load. This prevents the system from being overloaded, enhances reliability, speed, and ensures that the workload is maintained evenly throughout the servers. Depending on the application’s performance and redundancy needs, load balancing can be done using round robin, least connections, and IP hash.
Caching
Performance efficiency increases with improved content caching. A reverse proxy can store static assets such as images, scripts, stylesheets, and other items that need to be accessed frequently. In the case that users request the same assets repeatedly, the proxy will serve the content directly from the cache. This proxy reduces latency and enhances server load, delivering content faster for users in different geographical areas.
Security & Threat Mitigation
Hiding the Origin
Utilizing a reverse proxy improves security by concealing the real IP addresses of the backend servers. It prevents external users or attackers from interacting with the origin servers. This form of segregation lessens the prevalence of targeted attacks, unauthorized access, or data theft. Therefore, ensuring that the core components of the system remain undisclosed and secured.
Web Application Firewalls (WAF)
Many reverse proxies integrate with or act as a Web Application Firewall (WAF), also known as an Application Delivery Firewall. A WAF inspects and filters incoming traffic, blocking requests such as SQL injections, cross site scripting (XSS) and even zero exploits. With the WAF sitting on reverse proxy, organizations are able to mitigate common web-based attacks, preserve their reputation, remain compliant and protect user data.
SSL/TLS Encryption
A reverse proxy can manage SSL/TLS encryption through a process known as SSL termination. This allows the proxy to take on the burdensome task of HTTPS traffic, thus easing the load on backend servers. A SSL Reverse Proxy not only enhances performance, but also simplifies the management of SSL certificates while centralizing the governance of encryption and thus fortifying security policy.
Additional Benefits of a Reverse Proxy Server
Besides providing security and optimizing performance, a reverse proxy comes with a wide array of other operational advantages such as:
- Compression: Helps with optimizing transmission of data to clients, thus, data loads faster, and less bandwidth is consumed.
- A/B Testing: Assists in routing users to different versions of a site or app for Performance and UX benchmarking, thereby aiding in data-based evaluations.
- Centralized Logging: In consolidating logs from different servers, this feature helps with improving the analysis of the system’s performance as well as submitting reports for compliance analysis.
Implementing a reverse proxy server enables organizations to ensure faster application access, improved security and a dependable infrastructure. For a robust platform or a scaling web app, deploying a reverse proxy secures application delivery while enabling a shift towards a more scalable architecture.
Considered as a foundational feature in addressing web traffic and delivery concerns, reverse proxies serve as application accelerators for a modern application infrastructure.
In the real world, they’re broadly deployed to resolve issues in scalability, performance, and security. From SaaS startups to global enterprises, reverse proxy servers are foundational in managing modern web traffic and application delivery.
Use Cases of Reverse Proxy
There are Reverse Proxies in use in many different cases and industries:
- E-commerce stores and websites make use of reverse proxies so that they can process and handle thousands of user requests concurrently without hampered page loads, content delivery, and uptime during sales events or peak traffic periods.
- Media and video streaming services use reverse proxies for content caching and load balancing, enabling the delivery of high definition videos with significantly reduced buffering.
- SaaS services employ them for routing API calls, granting multi-tenant support and additionally shielding backend microservices from potential unauthorized access.
- Reverse proxies are employed in enterprise IT corporate environments for managing internal applications, enforcing stringent security policies, and monitoring application usage for remote access or partner integrations.
- This wide range of use cases for reverse proxies highlights the need for efficient performance and flexibly operational adaptability in a complex environment.
Global Server Load Balancing (GSLB)
A reverse proxy routing user requests to the data center that is nearest or most optimal for the user is a particularly distinct use case in large-scale operations. This kind of scenario is known as Global Server Load Balancing (GSLB).
GSLB achieves the following:
- Improved responsiveness due to a reduction in user-to-server latency.
- Improved availability. Traffic can be redirected to a different server in case of a server failure.
- Enhanced redundancy for recovery from disaster scenarios.
- Global Server Load Balancing (GSLB) enables firms to maintain consistent performance and global accessibility for their customers when paired with reverse proxies.
Modern Environments: Cloud-Native and Hybrid Deployments.
Reverse proxies serve distinct purposes in modern environments, such as within containerized systems and microservices. Reverse proxies serve to manage both external and internal traffic in a secure manner and are used through NGINX, Envoy, and HAProxy in Kubernetes clusters. Read the guide on what is kubernetes.
In Hybrid settings, an organization’s private infrastructure mixes with on-premise public clouds. This creates a distinct need for secure traffic management which reverse proxies serve as secure traffic managers. The ability to enforce uniform guidelines and rules while consolidating monitoring systems enables effective management for intersectional environments.
Managing outmoded systems alongside scaling clouds is made simple through reverse proxies as they offer the control and interoperability vital in today’s environments.
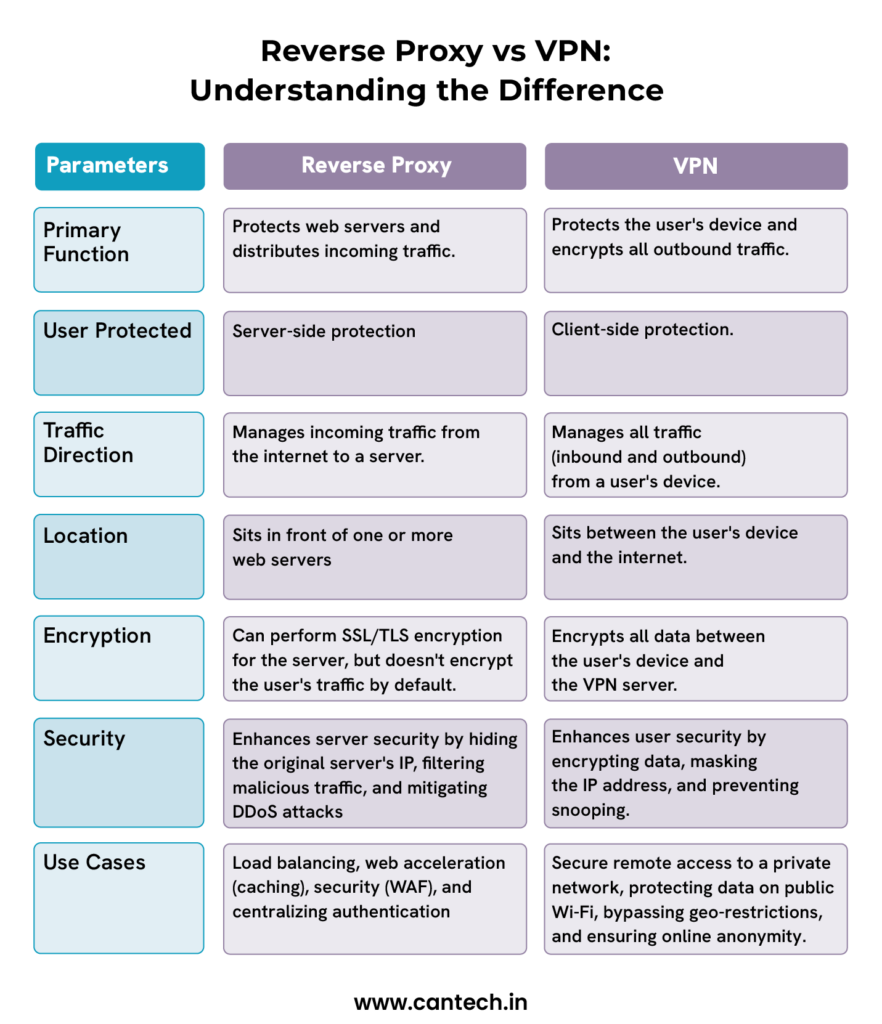
Reverse Proxy vs VPN: Understanding the Difference
VPNs are centered around aiding private secure access while reverse proxies manage web traffic, applications, and performance. Both serve crucial roles, however, in completely distinct manners.
In order to deliver prompt, secure, and reliable digital impressions, reverse proxies have become more crucial than ever. Among other things, as businesses expand globally and hybrid or cloud-native models, reverse proxies still serve as a single checkpoint for intelligent traffic control and application delivery.
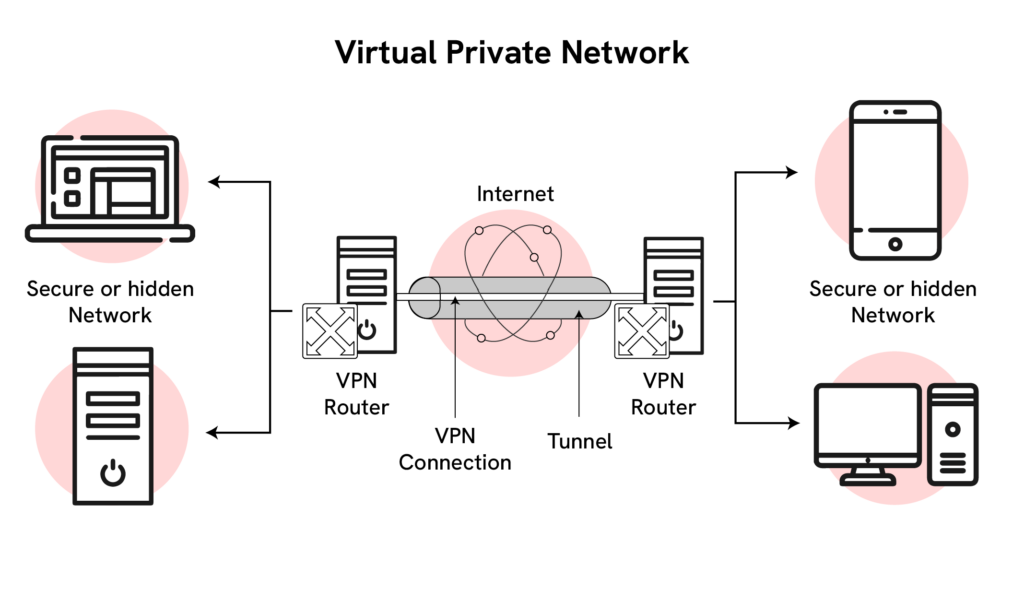
How VPN Works?
A Practical Guide: Configuring a Reverse Proxy
Improving traffic management, enhancing protection, and boosting performance can be achieved easily by configuring a reverse proxy. Having control over a single application, or a more complicated enterprise-grade infrastructure, management becomes easier with a reverse proxy which grants command over clients’ requests.
Setting Up a Reverse Proxy: Overview
The first step towards configuring a reverse proxy would be to position the proxy server in front of the application or web servers. This allows the reverse proxy to intercept all incoming HTTP or HTTPS requests for processing. Processing includes everything the proxy must do prior to sending the information to the backend server. The basic setup includes:
- Reverse proxy software installation, some examples are NGINX, Apache, or HAProxy.
- Routing rules creation for certain ports or URLs to backend servers.
- If HTTPS traffic requires decryption (SSL termination), make certain that SSL/TLS is enabled.
- Lastly, be sure to test the setup to guarantee proper routing, performance, and security.
- A deployment strategy can dictate whether the containerized environment, the cloud, or the onsite setup is more suitable.
Reverse Proxy Software: Popular Tools
The list below contains some of the most common open-source and commercial reverse proxy solutions that can be adapted to different types of deployments:
All of these solutions provide different benefits and depending on your infrastructure, scalability needs, and level of expertise, some will be better suited than others.
Step-by-Step Example: NGINX Reverse Proxy Configuration
To demonstrate how simple it is to configure a basic HTTP reverse proxy using NGINX, here’s a practical example:
Prerequisites:
- NGINX installed on your server
- Access to a backend server running on a different port or IP (e.g., localhost:3000)
- Basic NGINX Configuration File (/etc/nginx/sites-available/reverse-proxy.conf):
server {
listen 80;
server_name yourdomain.com;
location / {
proxy_pass http://localhost:3000;
proxy_http_version 1.1;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
}
Steps to Enable:
- Save the configuration file to the sites-available directory.
- Create a symbolic link to sites-enabled:
sudo ln -s /etc/nginx/sites-available/reverse-proxy.conf /etc/nginx/sites-enabled/
- Test the configuration:
sudo nginx –t
- Reload NGINX:
sudo systemctl reload nginx
Using a reverse proxy server improves the performance, protection, and scalability of web services whether an individual application is being tuned or in a multi server design being developed, Adapted a simplified phrase.
Conclusion
A reverse proxy acts as the critical intermediary server in front of one or more web servers. They accept the responses from the web servers that issue client requests. And also separate the web servers from the users and act as a filter. Placing a reverse proxy in front of the web servers aids in centralization of the incoming traffic stream and improves the services. They are better secured, the performance of the web services improves, the system’s overall reliability has enhanced.
Some of the critical roles that the proxy can perform are the management of the network traffic to servers as well as the management of the SSL encryption, offloading the crypto work to other servers.
Most importantly, the reverse proxy is also a critical security port as integrated with web application firewall (WAF), stops web application attacks and hides the servers from view. Streamlines the management of servers by presenting a single public access point to the application, irrespective of the application’s server infrastructure.