Overwhelming a target with fake traffic spikes might seem easy, but it is one of the most powerful methods to bring systems crashing down. So, how widespread are Distributed Denial of Service (DDoS) attacks, and what level of damage do they cause?. As per recent reports, there has been a staggering 108% increase in DDoS attacks worldwide in 2024.
This blog explores what DDoS attacks are and How to defend against DDoS attacks.
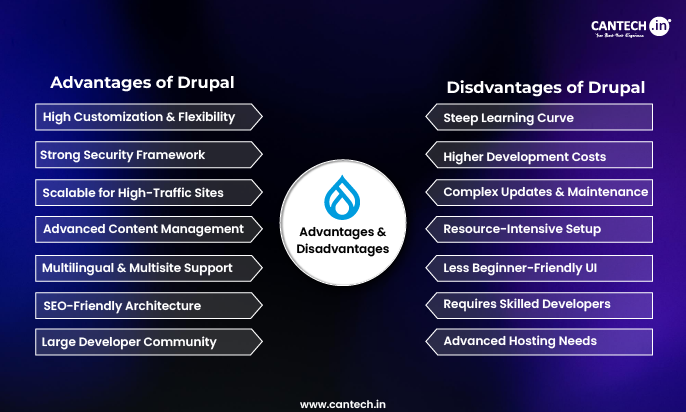
DDoS Attack Meaning
A Distributed Denial-of-Service (DDoS) attack is a type of cybercrime when an attacker overwhelms a server with excess traffic that renders connected websites and online services accessible to legitimate users. The reason behind DDoS attacks are as varied as the individuals and groups that launch them. Some attacks are driven by personal grievance or activism and others there are financially motivated.
In some cases, competitors may try to cripple a competitor’s online operations to divert a business in their favor. Extortion is also common: attackers flood a company’s servers, sometimes deploying ransomware or hostageware and demand large payouts to restore normal operations.
Difference between DoS and DDoS
The difference between a DoS and DDoS attack lies in scale. A DoS (Denial-of-Service) attack involves a single system which targets another system. Whereas a DDoS (Distributed Denial of Service) attack uses multiple systems simultaneously to overwhelm a single target. Beyond this, there are other several key differences:
| Aspect | DoS (Denial-of-Service) | DDoS (Distributed Denial of Service) |
| Source of Attack | Single systems attack a target system. | Multiple systems attack a single target simultaneously. |
| Detection | Easy to detect and block as it comes from a single source. | Difficult to detect as it comes from multiple sources. |
| Speed of Attach | Slow and limited by single systems capacity. | Faster and uses multiple systems for high impact. |
| Traffic Volume | Generates low traffic volumes. | Produces high traffic volumes which quickly overwhelms the system. |
| Method of Attempt | Uses tools or script from one machine. | Uses botnets controlled by a command and control server. |
| Source Tracing | Easier to trace back to origin | Tough to trace due to distributed nature and botnets. |
Types of DDoS Attacks
Here’s a breakdown of 4 different types of DDoS Attacks:
Volumetric Attacks
Volumetric attacks are the most prominent DDoS attacks. They use a botnet to flood a network or server with excessive traffic, exceeding its bandwidth and processing capacity. This results in network congestion and complete denial of service.
Protocol Attacks
Protocol attacks exploit vulnerabilities in network protocols like TCP. By initiating but never completing a TCP handshake, attackers leave server ports busy and unresponsive which eventually are overwhelming and shutting down the server.
Application Layer Attacks
Application Layer Attacks are also called layer 7 attacks, these attacks target the application layer by sending what looks like a legitimate user request. They slowly exhaust server resources which makes it difficult for companies to detect and defend against them.
Fragmentation Attacks
Fragmentation attacks exploit the IP datagram fragmentation process. Attackers send malformed or fake data packets that cannot be reassembled, consumes server resources and disrupt usual traffic management.
How DDoS Attacks Work
A DDoS attack takes the normal functioning of an online service and pushes it more than the allowed limits. For instance, a website handles only a specific number of requests per minute. When that threshold exceeds whether by legitimate surges, like an e-commerce site during black friday or ticketing platform for major events, performance degrades and the site may even crash.
In a DDoS attack, this overload is intentional. Attackers flood the target with high traffic from multiple systems, which overwhelms its capacity at various levels:
- Web Applications: Limited to a certain number of requests they can process simultaneously.
- Networks: Restricted by bandwidth which attackers can saturate with fake traffic.
- Servers: Have limits on the number of active connections they can handle.
If any of these thresholds are bypassed, the system becomes unavailable to legitimate users which leads to Denial-of-Service (DOS) attack.
How to Protect Against a DDoS Attack
Here’s a breakdown of how to protect against a DDoS attack:
Act Quickly
The sooner a DDoS attack is detected, the faster you can mitigate the damage. Businesses should implement DDoS protection technologies or services capable of identifying and managing abnormal traffic increases in real time.
Configure Firewalls and Routers
Set up firewalls and routers to block illegitimate traffic properly. Ensure they are regularly updated with security patch updates to stay protected against evolving threats.
Utilize Artificial Intelligence
While traditional defenses like advanced firewalls and intrusion detection systems are important. AI powered solutions are now being developed to identify and neutralize DDoS attacks proactively.
Secure IoT Devices
Prevent your Internet of Things (IoT) devices from being hijacked into botnets. Install security software and keep all devices updated with the latest firmware and security patches.
Conclusion
A proactive strategy with advanced security measures, latest updates, and rapid response is important to mitigate DDoS attacks and ensure uninterrupted access to online networks and services.
FAQ’s
What is a DDoS botnet?
A DDoS botnet is a group of devices which have been infected by malware or malicious software and have come under the control of a cyber attacker. They can be designed to achieve malicious tasks such as stealing sensitive data, sending spam, ransomware, fraudulently clicking on ads or distributed denial-of-service (DDoS) attacks.
Why is DDoS used?
DDoS attacks are used as a diversion by bringing down one area of a network or an application to manipulate security teams away from key assets to restore availability. Cyberattacks launch DDoS attacks for many reasons such as financial gain, geopolitical interests and more.
What are some examples of a DDoS attack?
Some of the most common examples of DDoS attacks are UDP flooding, SYN flooding and DNS amplification.