So in the enormous, interlaced world of cloud computing (where thousands of servers talk to each other at once) how are we to avoid digital havoc? How do we make sure the sensitive information of the billing department does not follow the unsecure web servers or the development traffic does not slug down the production programs?
The solution is not physically separating it, rather logical, virtual separation. This is the world of the Virtual Local Area Network or VLAN. VLANs are a basic technology that is supported by both the traditional and the modern cloud environment and serves as a platform that offers the framework and security to create efficient, scalable, and secure networks in the cloud.
This manual will clear up VLANs. We will define Virtual LAN, the principles of how VLANs operate, look in depth at the salient features of VLANs, and unravel the important benefits of VLANs (and the little bit of drawbacks) that have made them essential in cloud computing.
What is a Virtual LAN?
So, what is a VLAN? The acronym VLAN is used to refer to Virtual Local Area Network. A VLAN is fundamentally a subdivision of a physical network that is based on logic. It enables a physical network switch to be divided into many, autonomous broadcast domains.
Consider a physical network switch (office building) of large size having numerous departments. You can use ingenious and movable partitions to create separate and distinct team spaces instead of erecting separate and physical walls that are costly and unmoveble to accommodate each department. These partitions are VLANs. Individuals in the same partition (VLAN) will be able to communicate with other people without much difficulty but to communicate with an individual in another partition, they will have to pass through a central gateway (a router or a layer 3 switch).
What is the purpose of a VLAN?
Its main aim is to subdivide a big, flat and broadcast-intensive network into small and manageable, as well as secure segments. This logical segmentation is important in the cloud environment where multi-tenancy, the provision of hosting resources to multiple customers or departments is the norm.
The VLANs Magic of 802.1Q Tagging
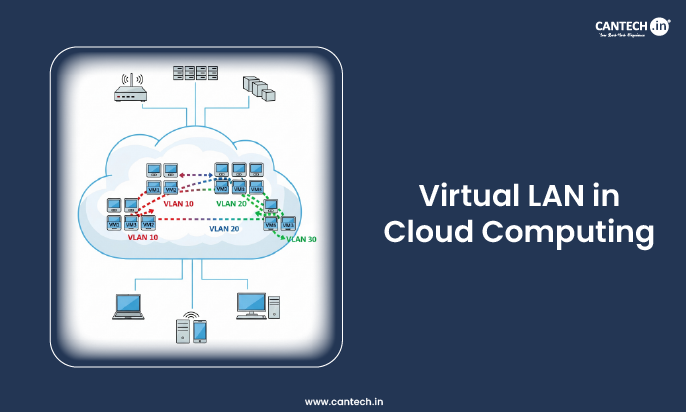
How do VLANs work? It works by a process known as tagging (standardized by the IEEE 802.1Q protocol).
In a conventional network, a switch sends data frames along on the basis of MAC addresses and there is no knowledge of logical separation. You also attach each switch port to a particular VLAN when configuring a VLAN (e.g., VLAN 10 of Web Servers, VLAN 20 of Database Servers).
Access Ports: A device (such as a server) attached to an access port transmits a frame which the switch picks up and adds a VLAN tag, a 4-byte header which is added to the Ethernet frame. This tag has VLAN ID (e.g. ID 10).
Internal Switching: This frame is now only forwarded via other ports which are a part of the same VLAN (VLAN 10). The frame will not be seen in ports designated to other VLANs, which is isolation.
Trunk Ports: A trunk port is required to transport traffic across a physical link (e.g. between two switches, or between a switch and a cloud router) that will carry traffic on more than one VLAN. This port is aware of 802.1Q tags and it leaves them untouched when traffic is being transmitted between devices.
It is this tagging mechanism that allows one physical network infrastructure to be used to support many isolated virtual networks.
Key Features of VLAN: Beyond Basic Segmentation
The features of VLAN technology provide a powerful toolkit for network administrators. Understanding these features is key to understanding why use VLAN architectures.
Broadcast Control
The typical characteristic of a VLAN is broadcast control. In a classic flat network a broadcast message issued by any one of the devices is relayed to all other devices in the same physical network segment. This all-to-all model of traffic rapidly causes a congestion as the network expands and wastes valuable bandwidth, requiring each device to handle packets that are not of any interest to them. It can be solved with a VLAN which makes logical boundaries where broadcasts (such as ARP requests) stay in their respective VLANs.
The effect of such containment is heavy on performance and scalability of the network. VLANs allow a single badly configured or talkative device to have a restraining effect on the entire network infrastructure by confining the broadcast domain to fewer devices that are required. This is of particular concern to the contemporary cloud systems and huge enterprise networks, whereby thousands of devices can co-exist.
Security
VLANs serve as a primitive security barrier, which offers an important layer of network isolation. Devices in one VLAN are by default unable to communicate with the devices in another VLAN. By virtue of this isolation, an attacker is not allowed to directly reach sensitive systems through a router or firewall even when a foothold is achieved on a device within a less secure VLAN, say a public guest WiFi network, even though such a device will still be within a packet-tagged different VLAN. This architecture implements the less privilege principle at the network level.
This isolation forms the foundation of construction of trusted network layouts such as Demilitarized Zones (DMZs). As an example, vulnerable to the public internet, web servers can be stored in a single VLAN, in a second one can be application servers, and in a third can be highly sensitive databases. These VLANs can then be prohibitively restricted and regulated in terms of their communication with each other, via its respective firewall policies and Access Control Lists (ACLs) on the routing device linking them. Such an arrangement will guarantee a restricted flow of traffic between segments to what has been specified and authorized, minimizing the attack surface and limiting the potential attack.
Improved Performance
Effectiveness of broadcast control, as well as, isolation of traffic is what leads to performance advantages of VLANs. The VLANs also minimize the total network congestion by removing unwanted broadcasts and multicasts among the other segments. This saves bandwidth available to legitimate unicast application data which is the type of traffic that directly affects user experience and business operations. The outcome is a less latent and more throughput-intensive network in the most important applications.
This performance improvement is especially crucial to latency sensitive and high bandwidth applications that are common in latency-and bandwidth-sensitive cloud computing and contemporary data centers. Activities such as live video streaming, transferring of large files and replication of databases in real time need a constant and unhindered network support. An efficient white label OTT solution can leverage these high-performance networks to deliver seamless live streaming and on-demand video experiences without interruptions VLANs make sure that this traffic is neither deterred nor slowed down by unnecessary broadcasts of other departments or types of services.
Simplified Management
VLANs introduce the abstraction layer that makes network management and administrative overhead very simple. Logical workgroups are not confined to physical location, but may be defined by organizational function instead (e.g. “Marketing,” “Engineering,” “Printers”). It implies that the users of the same logical group may be located anywhere in a building or a campus without the need to physically modify the physical cabling infrastructure.
Such rational management is transferred to unrivalled agility and operational efficiency. When the employee transfers to a different department, it does not need physical transfer of the network jack as the network administrator would do. Rather, they need only to reconfigure the port on the network switch to reassign it to the new VLAN instead of the old one. This modification is possible immediately by use of software, which reduces down time and simplifies IT processes.
VLAN and Its Types: Static, Dynamic, and More
There are several ways to assign a device to a VLAN. The main types of VLAN membership are:
- Static VLAN (Port-based VLAN): This is the most popular and easy one. A switch port is configured to be a member of a particular VLAN in the configuration of an administrator. Any device that is connected to that port joins that predetermined VLAN. It is safe and simple to handle.
- Dynamic VLAN: It is a more flexible mechanism whereby a device is put in a VLAN according to its attributes rather than the physical port itself. This is normally done by a policy server (such as a RADIUS server).
- MAC-based VLAN: It is assigned depending on the unique MAC address of the device. When a device is connected, the switch consults a database to define the VLAN in which the device is to be located.
- Protocol VLAN: This can be assigned to a protocol depending on the protocol the device uses (i.e. IPv4, IPv6 etc.).
- VLAN Trunking Protocol (VTP): VLAN Trunking Protocol (VTP) is not a kind of VLAN, but a Cisco-proprietary protocol that can be used to manage the VLAN settings of many switches. It enables an administrator to add, delete or rename VLANs on one VTP server switch and these changes are automatically transferred to the rest of switches within the VTP domain making them consistent.
Advantages of VLANs: The Compelling Case for Virtualization
The benefits of VLANs are what have cemented their role as a non-negotiable aspect of network design, especially in the cloud.
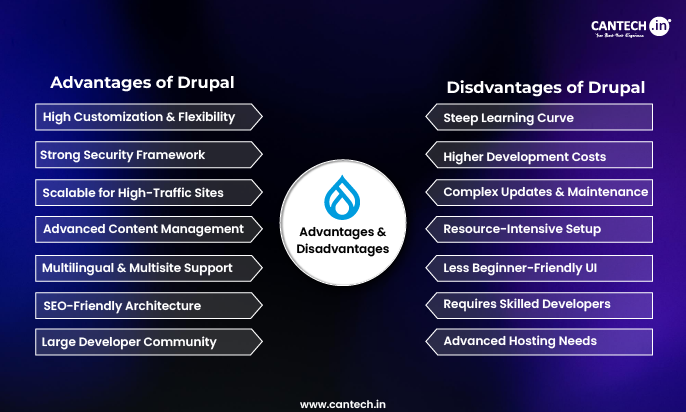
Enhanced Security
VLANs enhance an extra security layer since sensitive data and critical systems are kept out of the rest of the network. VLANs are used to separate systems as opposed to a single, flat network, where all devices would be interconnected. It implies that in case an attacker hacks into a vulnerable station on a weaker network (a public Wi-Fi VLAN) he is not connected to sensitive locations like financial databases, HRs, or production servers. Any traffic to leave one VLAN and enter into another has to pass through a router or a firewall where security policies, ACL, and intrusion detection systems can inspect and regulate traffic.
This division reduces the effects of attacks and eliminates movement across the network. VLANs can also isolate the infection to one segment in a situation where malware is being passed which minimizes the total risk. This is in accordance with the principles of Zero Trust security whereby no device or user is automatically trusted just because they are within the network. Through the association of VLAN segmentation with powerful access control lists and monitoring, organizations form a strong security position, which prevents both external and internal threats.
Cost Efficiency
Historically, segmenting the network required the purchase of extra physical switches, routers, and firewalls that could be used to divide traffic. VLANs reduce much of these overheads as logical segmentation can be done on a similar physical switch infrastructure. This saves a lot of capital (CapEx) and puts into good use the hardware invested in. The isolated networks of the same switch fabric give organizations the opportunity to create several isolated networks without the requirement to create a distinct physical network to serve each department or project.
VLANs may also be used to save on operations beyond hardware. Software-defined changes enable network administrators to make changes on their networks quickly (expanding or reconfiguring network segments), or to make changes without the need to physically rewire equipment or buy new equipment. This dynamism reduces the maintenance work, less downtime has been experienced in changing the networks, and it helps to achieve better utilization of resources, all with a very high level of network performance and security.
Increased Flexibility and Agility
Existing data centers, particularly those serving cloud-based applications, need to be high-performing in provisioning and scaling. VLANs enable an administrator to dynamically create network segments to ensure a new workload, a virtual machine, or a container is dynamically assigned to the appropriate logical network segment. This will remove the manual procedures to manually configure the more complex virtual machines whenever a workload is transferred between servers, racks, or even datacenters.
This dynamism allows companies to react fast to changing needs. As an illustration, an application tier can be instantly deployed in a VLAN with appropriate security and QoS policy irrespective of its physical location. This does not only reduce the deployment times but also provides uniform network behavior throughout the infrastructure. Consequently, the use of VLANs is a necessity in attaining the agility in operation of the hybrid clouds and DevOps-oriented environments.
Simplified Project and Departmental Management
With VLANs, it becomes more simple to do business-based network organization as opposed to the physical topology. As an example, a specific VLAN can be made in the Finance Department which contains all users and servers of that department and they may be distributed over different floors, different campuses, different branch offices. The rationale behind this logical grouping is that it makes it easy to enforce the policies such that the sensitive financial data is only accessed by the authorized users and the traffic of other departments is not mixed up.
This allows administration of a network to be simpler and error-free in terms of management. Access control lists (ACLs), quality-of-service (QoS) and security policies can apply to full VLANs instead of applied to each individual device by IT teams. This centralized nature makes it easier to manage the networks and reduces misconfigurations as well as gives more insight into the traffic patterns to allow organizations to ensure compliance with regulatory requirements and internal governance standards.
Disadvantages of VLANs: Understanding the Limitations
While powerful, VLAN technology is not without its challenges. Acknowledging the disadvantages of VLANs is crucial for proper implementation.
- Configuration and Management Complexity: VLANs introduce complexity in configuration when they make logical management simpler. Poor configuration like trunking wrong or failure to have VLAN tags may cause security gaps or network failure. Such protocols as VTP may be problematic when not properly configured.
- VLAN Hopping Attacks: VLANs are also very secure, but they can be attacked by certain other attacks such as VLAN hopping, in which an attacker can use VLANs to implant 802.1Q tags to direct traffic to a VLAN they are not supposed to access. This necessitates a cautious switch configuration in order to counter.
- Scalability Limits: VLAN ID field A regular 802.1Q tag has a 12-bit VLAN ID field, and defines VLANs to 4,096 (0 and 4095 are reserved). Although this is sufficient in the majority of enterprises, very large cloud providers and service providers need more advanced technologies such as VXLAN in order to overcome this limitation.
- Inherent Latency: As previously noted, although the tagging and untagging of frames is usually low, there is a small latency processing overhead and latency incurred by the process. This is inconsequential to most applications, but when ultra-high-performance trading or HPC clusters are needed, it is a factor.
VLANs in the Modern Cloud Context
The fundamental principles of VLANs are conceptually hidden in a modern public cloud (AWS, Azure, Google Cloud) and expressed in software-defined networking (SDN). Switch ports are not configured manually.
You instead make Virtual Private Clouds (VPCs) or Virtual Networks (VNETs) which is the clouderrr era version of the VLAN concept. In a VPC, you make subnets that are essentially similar to VLANs, giving you logical isolation, a security boundary (with security groups and NACLs), and routing that is under control. All the underlying 802.1Q tagging and physical network management is transparently managed by the SDN controller of the cloud provider.
Conclusion: The Virtual LAN has a Long History.
Virtual Local Area Network owes its existence to the strength of logical abstraction. VLANs have brought the efficiency, security, and manageability levels that the network architecture had never known before by decoupling network architecture and physical hardware.
The notion of what a VLAN is and how it functions is a fundamental requirement of any network engineer, cloud architect or cybersecurity specialist. Although implementation has now been altered by developing physical switch configuration into software-defined cloud control panels, the fundamental concepts of segmentation, broadcast control and logical isolation are still more than relevant.
Since it has been facilitating secure multi-tenancy to more intricate cloud architectures, the VLAN is a grid, the grid that is not seen, but is still needed to impose order into the digital mess that modern computing is.